Web sign in is a new feature enabled by Microsoft, to allow users to login to their PC using the standard windows login prompt. Users also get any MFA prompts sent my this login, as well as enforcing conditional access policies for signin.
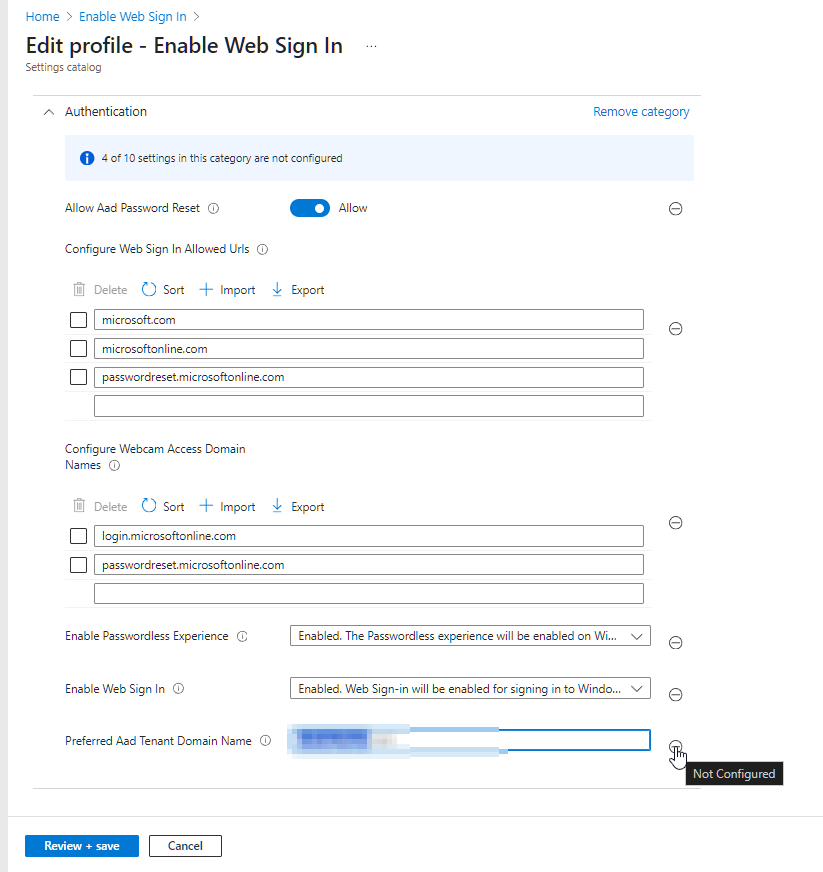
Organizations adopting Microsoft’s Web Sign-in (passwordless) feature often leverage the PreferredTenantDomainName setting in Intune to pre-populate users’ Azure AD suffix on the Windows lock screen. However, this same setting can inadvertently break local account authentication for UAC prompts—appending the Azure AD domain to any credentials you type and causing elevation failures.
In my brief testing, the ONLY thing this impacts is the auto population of the domain on login. so instead of the user just typing “myusername”, they have to type “myusername@contoso.com” every time they login.
The Issue
When PreferredTenantDomainName is configured under the Intune CSP
./Device/Vendor/MSFT/Policy/Config/Authentication/PreferredAadTenantDomainName
it writes to the registry at:
HKLM:\SOFTWARE\Policies\Microsoft\AzureADAccount\PreferredTenantDomainName
With this value present, any UAC prompt that asks for credentials forces the domain suffix onto local-SAM accounts (e.g. turning .\Administrator into Administrator@contoso.com), which of course doesn’t match and denies access.
Solution
To restore classic UAC behavior, simply remove the PreferredTenantDomainName entry from the registry. Once cleared, UAC will accept local-SAM credentials normally without appending the Azure AD suffix.
PowerShell Script
# Run as Administrator
$regPath = 'HKLM:\SOFTWARE\Policies\Microsoft\AzureADAccount'
$value = 'PreferredTenantDomainName'
if (Test-Path $regPath) {
Remove-ItemProperty -Path $regPath `
-Name $value `
-ErrorAction SilentlyContinue
Write-Host "Removed $value from $regPath"
} else {
Write-Host "Registry path not found; nothing to do."
}
Registry CLI
reg delete "HKLM\SOFTWARE\Policies\Microsoft\AzureADAccount" /v PreferredTenantDomainName /f
Deployment via Intune
- In your Intune configuration, under Device restrictions > Authentication, clear the Preferred AAD tenant field.
- Sync devices, or push a restart.
- Verify that UAC elevation dialogs now accept local‐SAM credentials without domain suffixes.
By removing the PreferredTenantDomainName setting, you can continue to benefit from Web Sign-in on your lock screens while preserving the ability to authenticate with local accounts in UAC prompts.